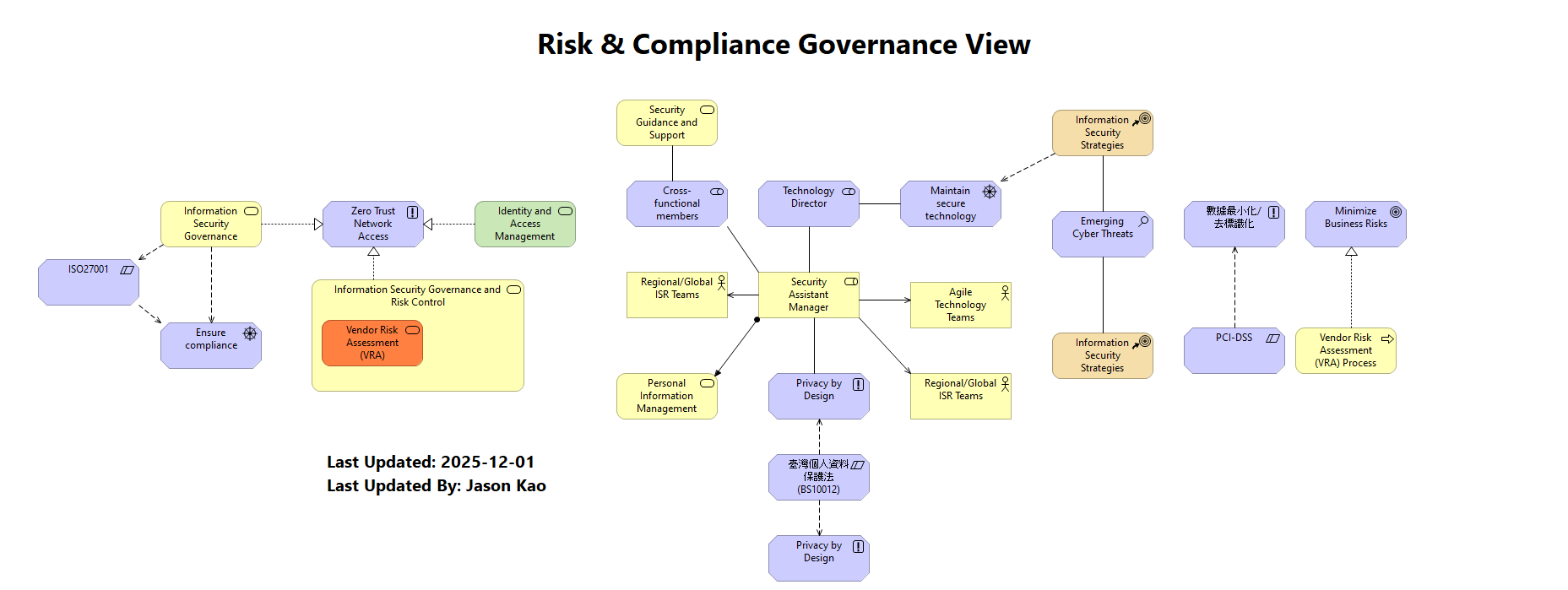
說明法規限制如何驅動治理原則,並透過業務服務實現合規管理。
1. 法規要求(如臺灣個資法 )如何驅動 CISO 確立的 隱私設計原則 (Privacy by Design) 。
2. 治理服務(如 Security Governance and Risk Control )實現了 CISO 訂定的 ZTNA 原則 。
3. 核心角色(Security Assistant Manager )負責執行 重要的合規服務,如 PIMS 倡議 和 VRA(供應商風險評估),以最小化業務風險 。
| Last Updated | 2025-12-01 |
| Last Updated By | Jason Kao |